Atmos Terraform Apply
Simplify provisioning Terraform entirely from within GitHub Action workflows. This action makes it very easy to apply that changes from a terraform plan from directly within the GitHub UI. Use this action in your workflows to apply changes to your infrastructure.
Given any component and stack in an Atmos supported infrastructure environment, github-action-atmos-terraform-apply will retrieve an existing Terraform planfile from a given S3 bucket using metadata stored inside a DynamoDB table, run atmos terraform apply with that planfile, and format the Terraform Apply result as part of a GitHub Workflow Job Summary.
This action is intended to be used together with Atmos Terraform Plan, as well as integrated into drift detection with Atmos Terraform Detection and Remediation GitHub Actions.
Features
This GitHub Action incorporates superior GitOps support for Terraform by utilizing the capabilities of Atmos, enabling efficient management of large enterprise-scale environments.
- Implements Native GitOps with Atmos and Terraform tightly integrated with GitHub UI
- No hardcoded credentials. Use GitHub OIDC to assume roles.
- Compatible with GitHub Cloud & Self-hosted Runners for maximum flexibility.
- Beautiful Job Summaries don't clutter up pull requests with noisy GitHub comments
- 100% Open Source with Permissive APACHE2 License means there are no expensive subscriptions or long-term commitments.
Screenshots
In the following screenshot, we see a successful "apply" Job Summary report. The report utilizes badges to clearly indicate success or failure. Unnecessary details are neatly hidden behind a collapsible <details/> block, providing a streamlined view. Additionally, a direct link is provided to view the job run, eliminating the need for developers to search for information about any potential issues.
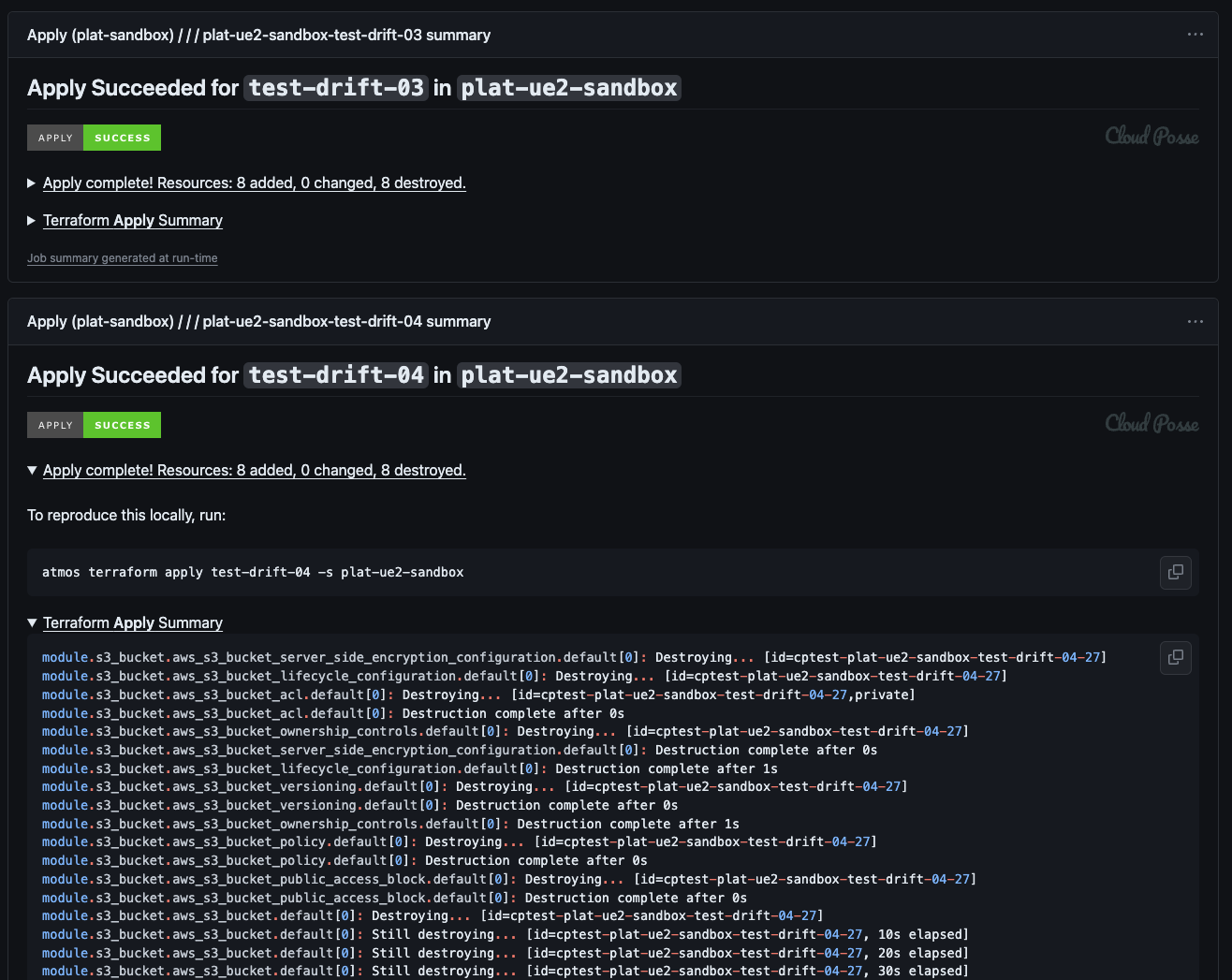
Usage Example
In this example, the action is triggered when certain events occur, such as a manual workflow dispatch or the opening, synchronization, or reopening of a pull request, specifically on the main branch. It specifies specific permissions related to assuming roles in AWS. Within the "apply" job, the "component" and "stack" are hardcoded (foobar and plat-ue2-sandbox). In practice, these are usually derived from another action.
We recommend combining this action with the affected-stacks GitHub Action inside a matrix to plan all affected stacks in parallel.
atmos-terraform-apply.yaml
GitHub Actions support 256 matrix jobs in a single workflow at most! When planning all stacks in an Atmos environment, we frequently plan more than 256 component in the stacks at a time. In order to work around this limitation by GitHub, we can add an additional layer of abstraction using reusable workflows.
atmos-terraform-apply-matrix.yaml
Requirements
This action has the requirements as Github Actions. Use the same S3 Bucket, DynamoDB table, IAM Roles and config described there.

